Defeating Persistent Web Fingerprinting with Chameleon
The Web Fingerprinting Series (Dispatch No. 1)

Browser Fingerprint Tracking
The seemingly mundane activities you engage in every day on your computer might seem somewhat uninteresting to you, but in fact are quite valuable to those interested in tracking you across the web. Your data can be captured and commoditized by data brokers and sold to marketers.
Many believe that simply using a privacy-protecting web browser with a good ad blocker installed can elude the unique fingerprint trail their system leaves behind at every point of activity. This simply isn’t the case. A couple quick visits to fingerprint.com will dispel that notion quite readily.
There are many factors that come into play when you are seeking to achieve a secure and private web browsing experience. This series will focus on three key methods that must be employed in order to defeat persistent fingerprint tracking. They are as follows, the use of a trustworthy VPN, proper Firefox deployment and setup and effective deployment of essential web browser extensions.
The Chameleon Browser Extension
The first part of this series on evading web fingerprinting will focus on the Chameleon web browser extension. We will be looking at configuring it with Firefox as that is the recommended browser for privacy by us and others (privacyguides.org for instance), but it is also available for other browsers as well.
It isn’t so much about eliminating your fingerprint, but instead to automate the creation of a unique ephemeral fingerprint for regularly timed browsing sessions. And this is exactly what Chameleon allows you to do. This approach gives you the benefit of customizing your browser with the functionality you want while still protecting you from persistent tracking.
Deploying Chameleon
Installation
First, Install Chameleon and make sure the checkmark for ‘Allow this extension to run in Private Windows’ is enabled. You should see the window as shown below when clicking on Chameleon in the Firefox Toolbar:
It’s worth noting here that the ‘Home’ screen tab lists your spoofed ‘Current Profile’ and also allows you to ‘change’ it manually by clicking that button from this window.
Configuring the ‘Profile’ Tab
Once you enable Chameleon, you can then start with the ‘Profiles’ tab by invoking the extension from your Firefox Toolbar and clicking the second tab under the ‘Home’ tab:
As you can see from the screenshot above, I have configured Chameleon to use a ‘Random Profile’ for Desktop operating systems only as I have had issues with many websites breaking when reporting a Mobile operating system. It is also good to keep in mind that the duration specified under ‘Change periodically’ is how long of a session you want to browse as a given ephemeral user. I find 10 minutes a good balance between privacy and usability, but you can increase or decrease the duration to optimize for your ideal use case.
It is also useful to note that I have not had success on many websites when using the ‘Internet Explorer’ identifier, so under the ‘Windows’ tab I have turned off every version of that erstwhile browser. After having done that, performance and compatibility across the web has been much improved.
Configuring the ‘Headers’ Tab
There are a few important options that need to be enabled within the ‘Headers’ tab as illustrated below:
The ‘Do Not Track’ setting is redundant as it should be set directly in Firefox under Settings > Privacy & Security > ‘Send websites a “Do Not Track” request’.
‘Prevent Etag tracking’ should be enabled as it is an alternative method to cookies that can be used to track you across the web.
The ‘Spoof Accept Language’ setting can cause the inconvenience of a website loading a random language while you are visiting, so it is not recommended to use.
The ‘Spoof X-Forwarded-For/Via IP’ setting is used to obfuscate your IP address which is sometimes obtained through the use of these headers, but according to the developer does not work on many sites. Protecting your actual local IP address is something that should be achieved through the use of a reliable VPN.
The ‘Disable referrer’ option is a useful privacy protection to clear the referrer header or originating website before sending it to the destination website address. The developer mentions that while a useful setting, it can break some sites. I have had good luck with it enabled, however.
Configuring the ‘Options’ Tab
There are many important settings to configure in the Options/Injection tab. Let’s explore these below with both a screenshot of the recommended settings and an explanation of how they work:
The first setting, ‘Block media devices’ will not broadcast any built-in media devices on your computer to the current website. As shown above, I have opted for the ‘Spoof media devices’ setting to report media devices other than the actual ones built-in to my system. Using either of these options will protect you from revealing your true webcam or microphone hardware to websites.
‘Block CSS Exfil’ is a highly recommendable option that is useful in protecting against CSS attacks that attempt to steal sensitive data that you enter on web pages such as usernames, passwords, date of birth, social security numbers and credit cards.
‘Limit tab history’ will spoof the number of tabs you currently have open in your web browser window and should be enabled.
‘Protect keyboard fingerprint’ inserts a varying delay between keystrokes to obfuscate your unique typing patterns, which could be used to profile you. It also causes input fields to appear sluggish, so I opt to leave it off.
‘Protect window name’ should be enabled to keep you safe from being tracked across domains by clearing the window.name string value.
‘Spoof audio context’ is useful to protect you from being tracked across browsers through the fingerprinting of your device’s unique audio stack.
‘Spoof client rects’ protects against tracking of your unique client rectangle fingerprint across the web by spoofing its value.
‘Spoof font fingerprint’ should definitely be enabled to regularly report a different installed fonts set than the one actually installed that would normally make your system persistently unique. Your font fingerprint is otherwise able to be used in tracking you across browsers.
‘Screen Size’ can be automated to report a random resolution on-the-fly based on Chameleon’s currently generated user agent profile by choosing ‘Profile’ which is recommended for better protection.
‘Timezone’ should be set to ‘IP’ when using a VPN as Chameleon will acquire the correct timezone based on the IP address location (assigned by the VPN) of your browser upon launching Firefox. This timezone can be changed by simply changing your VPN server location and relaunching Firefox, which is an effective way to protect your persistent local timezone tied to your local ISP assigned IP address.
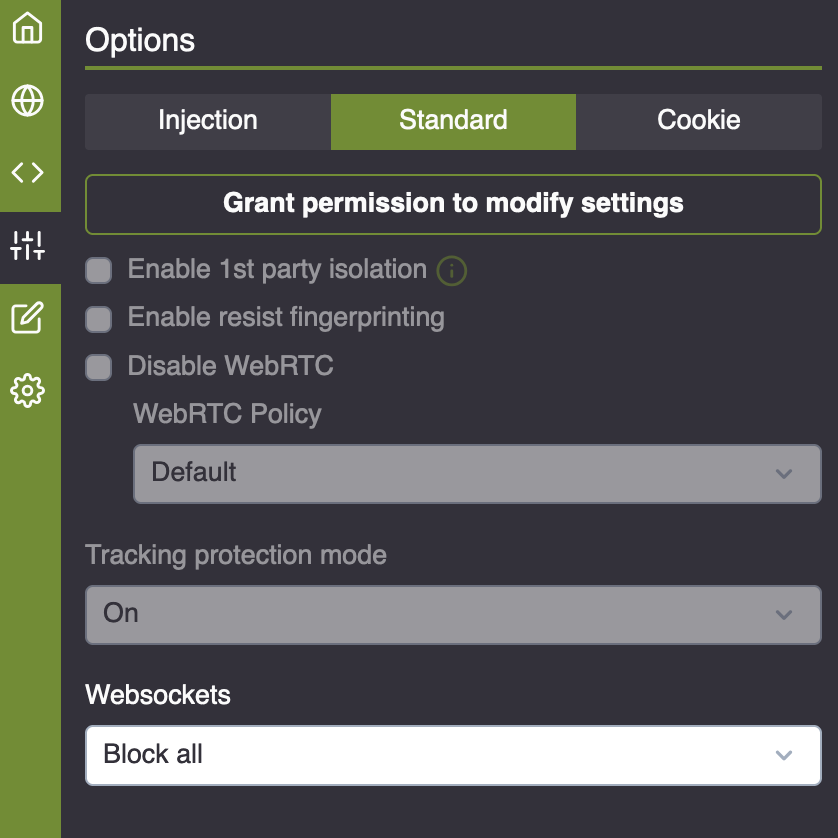
The rest of the settings under ‘Options’ are things that I like to configure directly within Firefox with the one exception being the option to set ‘Websockets’ to ‘Block all’ in the ‘Standard’ tab:
Accessing Settings
Clicking on the gear icon or ‘Settings’ tab will bring you to a special page in Firefox which looks like the one shown below:
From the Chameleon ‘Settings’ page you can also access the Wiki documentation which is quite helpful in describing the many different functions of the extension. It is also where you will find any websites you have created ‘Whitelist’ rules for.
Known Issues
Chameleon is not able to spoof your user agent headers when using certain sites. For instance, those using Cloudflare protections can cause an infinite captcha loop, so you can whitelist sites (from the ‘Whitelist’ tab in the Chameleon menu) where you regularly see this behavior occurring and use the Firefox ‘Real Profile’ setting or simply use an alternative browser like Safari for these situations. Similarly, Google sites that begin with accounts.google.com are exempt from Chameleon spoofing. This is another good situation to use Safari when logging in to your accounts.
Verifying Effectiveness
After proper configuration of Chameleon and the effective use of the other key methods mentioned above and expounded in this series, you will be able to defeat persistent fingerprinting of your web browsing activities.
One way to confirm you are no longer being fingerprinted is by visiting the popular tracking company fingerprint.com. They report the ability to track 99.5% of all internet users. By employing all the methods detailed in this series, you will be able to become one of the 0.5% of internet users they can’t track. This will be indicated by a welcome screen that says this is your first visit to their site and assigning you a unique identifier value that changes each time you quit Firefox and navigate to fingerprint.com in a fresh browsing session. If you are seeing a persistent unique identifier across fresh browsing sessions, this indicates the need to successfully incorporate the remaining methods from this series.
The Anti-Fingerprinting Series
I hope you have found this article a compelling start in a series highlighting the privacy concerns of web fingerprinting. Keep an eye out for Dispatch No. 2 which will focus on configuring the Security & Privacy settings of Firefox to achieve the best defense against fingerprinting and persistent tracking. Thanks for engaging with Apple Dispatch and please consider becoming a contributing Member to help support an outstanding community and a valuable continuing resource!
Helpful References:
Chameleon – Get this Extension for 🦊 Firefox (en-US)
https://addons.mozilla.org/en-US/firefox/addon/chameleon-ext/
Wiki | Chameleon
https://sereneblue.github.io/chameleon/wiki/
Stealing Data With CSS: Attack and Defense
https://www.mike-gualtieri.com/posts/stealing-data-with-css-attack-and-defense
Audio Fingerprinting using the AudioContext API
https://iq.opengenus.org/audio-fingerprinting/
Detect ClientRects Fingerprint
https://webbrowsertools.com/clientrects-fingerprint/
Window: name property - Web APIs | MDN
https://developer.mozilla.org/en-US/docs/Web/API/Window/name






Thinking about that I believe that my DNS filter + AdGuard filter is doing a similar job as this extension. I don't want to leave safari, but I really miss Mozilla and theirs extensions.