Defeating Web Fingerprinting and Tracking with Firefox
The Web Fingerprinting Series (Dispatch No. 2)

A Privacy-First Approach
Firefox is highly customizable and mature web browser that can be configured in powerful ways to enhance privacy.1 In this guide, we will focus our efforts on configuring Firefox to defeat both tracking2 and fingerprinting.3 It is also compatible with some of the best privacy extensions available. Foremost among them is uBlock Origin, which is essential for Firefox users as it effectively blocks a plethora of both ads and trackers across the web. Make sure you have installed uBO and enabled it to ‘Run in Private Windows’ before continuing with the rest of this guide.
We have already covered a vital part of the anti-fingerprinting equation with the Chameleon browser extension in our first dispatch of The Web Fingerprinting Series:
This guide works in tandem with the one written on Chameleon, so make sure to follow both of these guides and those to come to achieve an integrated secure web browser deployment. Also, please note that this guide was created for Firefox, version 129.
Let’s get started setting up Firefox to defeat tracking and fingerprinting by first exploring the problem of cookies.
Web Browser Session Cookies
Web cookies are an effective way for marketers and data collectors to track you across the web. Cookies are created within a particular browsing session and can even survive across sessions over long periods of time. Many don’t understand this fact and are being effectively tracked without their knowledge every time they go onto the web. By properly configuring Firefox, we can address this highly effective fingerprinting method.
Firefox Privacy Settings
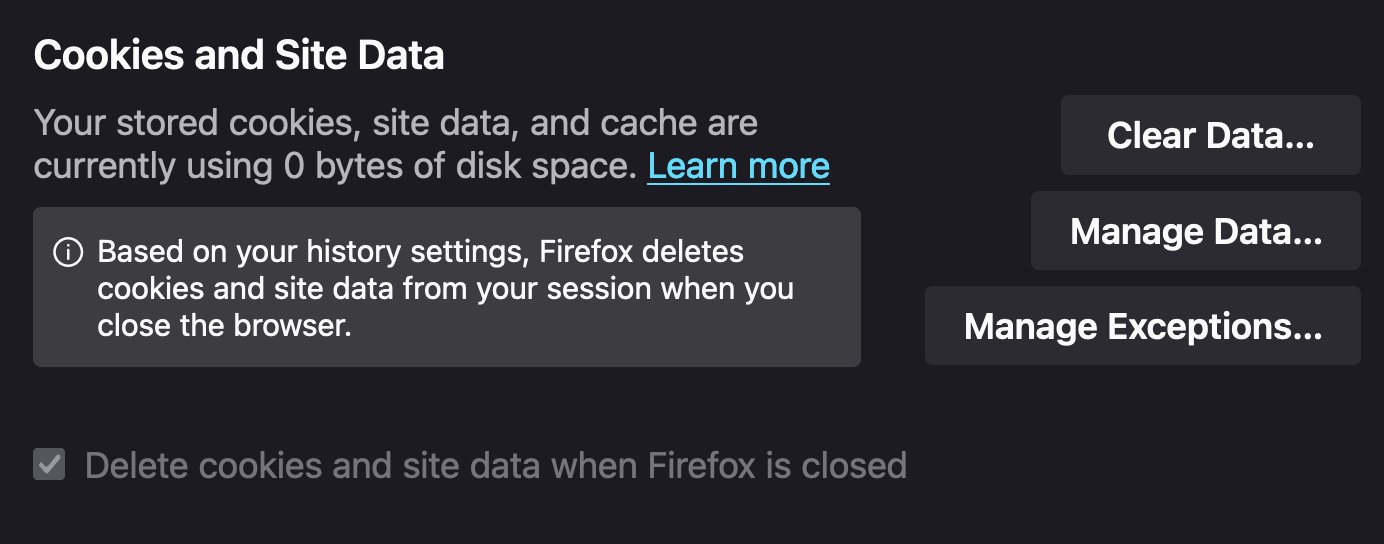
As you can see from the discussion above, it is vital to properly configure Firefox with a privacy-protecting cookie setting for each browsing session and an automatic clearing of currently cached cookies and other site data every time you quit the browser. Start by navigating to Firefox > Settings > Privacy & Security and scrolling down to ‘Cookies and Site Data’
Your settings should look like those below:
As you can see from the screenshot above the ‘Delete cookies and Site data when Firefox is closed’ is enabled. This is important to ensure that your browsing sessions cannot be persistently tracked over time. This setting is actually enabled automatically when turning on both ‘Use custom settings for history’ and ‘Always use private browsing mode’4 which you should enable under the ‘History’ section as shown below:
Also, by always using private browsing mode, Firefox will also not record your browsing history.
Browser Privacy
Scroll back to the top of the ‘Privacy & Security’ tab and under ‘Browser Privacy’ select ‘Custom’ with the settings shown below:
The settings selected in the screenshot above will give you a good balance between strong security and good compatibility as you browse various sites across the web.
Website Privacy Preferences
The ‘Tell websites not to sell or share my data’ is a relatively new initiative that actually has a legal framework behind it in many jurisdictions and should be enabled.5
Even though some reputable sources recommend turning of ‘Do Not Track’ as they argue it may actually be counterproductive, this setting should be turned on for clarity since according to Mozilla it is always on in Private Windows6 which is how you should be using Firefox by default for general browsing.
Firefox Data Collection and Use
Next you should scroll down to the settings under ‘Firefox Data Collection and Use’, and make sure to disable every option for sending any browser usage or telemetry data to Mozilla:
Website Advertising Preferences
A new setting recently introduced to Firefox is the ‘Website Advertising Preferences’:
Make sure that this setting is disabled as shown above for maximum privacy protection while browsing.
Security
Under the Security settings the first option, ‘Block dangerous and deceptive content’ queries your currently requested website and file downloads against a regularly updated database maintained by Google. Since you would be running some of your web activity through Google’s Safe Browsing Service (obfuscated or not)7 with this feature enabled, it is recommended to disable this option. Also, there are many other ways to block these kinds of threats through privacy-protecting DNS resolvers, DNS content blocker options in the Mullvad VPN app and by enabling DNS blocklists in the powerful firewall app, Little Snitch.
HTTPS-Only Mode
Even though most websites today are accessed with HTTPS over TLS (Transport Layer Security), it is a great idea to force this behavior by enabling ‘HTTPS-Only Mode in all windows’ which previously required an extension from the EFF called HTTPS Everywhere.
You can enable HTTPS-Only Mode in the Firefox Privacy & Security tab as show in the screenshot above.
DNS over HTTPS
‘DNS over HTTPS’ should be turned ‘Off’ since using a trustworthy VPN (like Mullvad) will provide their secure DNS servers which will provide better protection for your DNS connection requests.
However, if you are not using a VPN with Firefox, you should configure one of the DNS resolvers listed on Mullvad’s site8 or one recommended by Privacy Guides9 with the ‘Max Protection’ setting enabled.
Bonus Tip (WebRTC)
WebRTC is a technology to allow the playing of audio and video content in your web browser without the need for specialized plugins. It can also leak your actual IP address even when using a VPN.10 For that reason it is vital to disable WebRTC in Firefox with these steps:
In your address bar type ‘about:config’ and click ‘I accept the risk!’
Paste the following in the ‘Search preference name’ bar: media.peerconnection.enabled
Double-click the entry to change the setting to display ‘false’
You are now no longer at risk of leaking your actual IP address when using Firefox over a VPN!
Testing Your Privacy
As was mentioned in the first part of this series, a great way to test Firefox on your system is to see how you fair at the widely deployed fingerprint.com tracking company. This fingerprinting technology is broadly used across the web to persistently track Internet users. If you can’t defeat it across fresh browsing sessions then you are missing one of the key strategies discussed in this series.
Another great way to test both web tracking and ad blocking in your browser can be found at this GitHub tool. Run the test and see if you can get to 100% blocking of ads and trackers.
Looking Forward
In the guide following this one, the focus will be on how to properly deploy a VPN to protect your IP address and DNS queries to enhance protection against persistent fingerprinting and tracking. Keep an eye out for that dispatch to drop and thank you for reading!
Helpful References:
Privacy Respecting Web Browsers for PC and Mac
https://www.privacyguides.org/en/desktop-browsers/#recommended-firefox-configuration
SmartBlock for Enhanced Tracking Protection | Firefox Help
https://support.mozilla.org/en-US/kb/smartblock-enhanced-tracking-protection
Firefox's protection against fingerprinting | Firefox Help
https://support.mozilla.org/en-US/kb/firefox-protection-against-fingerprinting
Private Browsing - Use Firefox without saving history | Firefox Help
https://support.mozilla.org/en-US/kb/private-browsing-use-firefox-without-history
Global Privacy Control | Firefox Help
https://support.mozilla.org/en-US/kb/global-privacy-control
How do I turn on the Do Not Track feature? | Firefox Help
https://support.mozilla.org/en-US/kb/how-do-i-turn-do-not-track-feature
How does built-in Phishing and Malware Protection work? | Firefox Help
https://support.mozilla.org/en-US/kb/how-does-phishing-and-malware-protection-work
DNS over HTTPS and DNS over TLS
https://mullvad.net/en/help/dns-over-https-and-dns-over-tls
DNS Resolvers
https://www.privacyguides.org/en/dns/









That has not been published as of yet. Are there any specific topics you would like to see covered besides proper VPN deployment to avoid fingerprinting?
Was DIspatch no.3 ever posted?